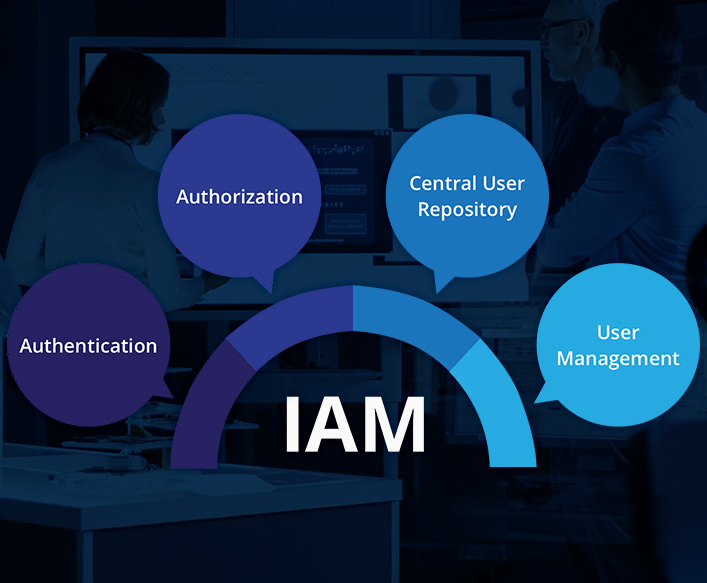
Security Challenges
- Lack of promptness in withdrawing access rights for a significant portion of employees leaving the enterprise.
- ntegrating cloud technologies with older, on-premise systems and centrally managing the governance of IT resources
- Failure to control the separation of duty (SoD), leading to possible fraud and financial losses
- Demonstrating rigidity in compliance with a growing number of regulatory requirements, including new data privacy rules in the European Union
- Lack of enterprise-wide transparency for access rights
- Controlling compliance costs associated with deploying flexible and scalable cloud-based identity governance
- Difficulty in monitoring toxic combinations of accumulated access rights
- Complex and insecure authentication of users for password resets
- ‘Least privilege’ principle is often not implemented